Cet article vous a-t-il été utile ?
Comment pourrions-nous l'améliorer ?
Administrator's Guide - Account Management
Service accounts allow applications to authenticate and access Lyve Cloud buckets and objects. The appropriate access and secret keys are generated when you create a service account. This information must be saved during the account creation, as you cannot recover key details afterwards. You must create buckets and assign permission to buckets before creating a service account. For more information, see Creating buckets and Creating bucket access permissions.
Role-based access to manage service accounts
The following table describes access to service account features based on your role.
| Actions | Admin | Storage Admin | Auditor (Read only) |
|---|---|---|---|
| Create service account | ✓ | ✓ | × |
| Edit | ✓ | ✓ | × |
| Clone | ✓ | ✓ | × |
| Delete | ✓ | ✓ | × |
| Status | ✓ | ✓ | × |
| List and view | ✓ | ✓ | ✓ |
| Service account expiration | ✓ | × | ✓ |
Creating service accounts
You must have at least one associated permission before creating a service account. To set the duration of keys generated after service account creation, you must first configure the expiration period. If the expiration duration is not set, the service account will not have an expiration set, and the secret credentials will never expire. For more information, see Setting expiration duration.
To create a service account:
- On the left-hand menu, select Service Accounts.
- Enter the Service Account Name.
- Select Permissions from the available list, and select Create.
- On the Service Accounts page, select Create Service Account.
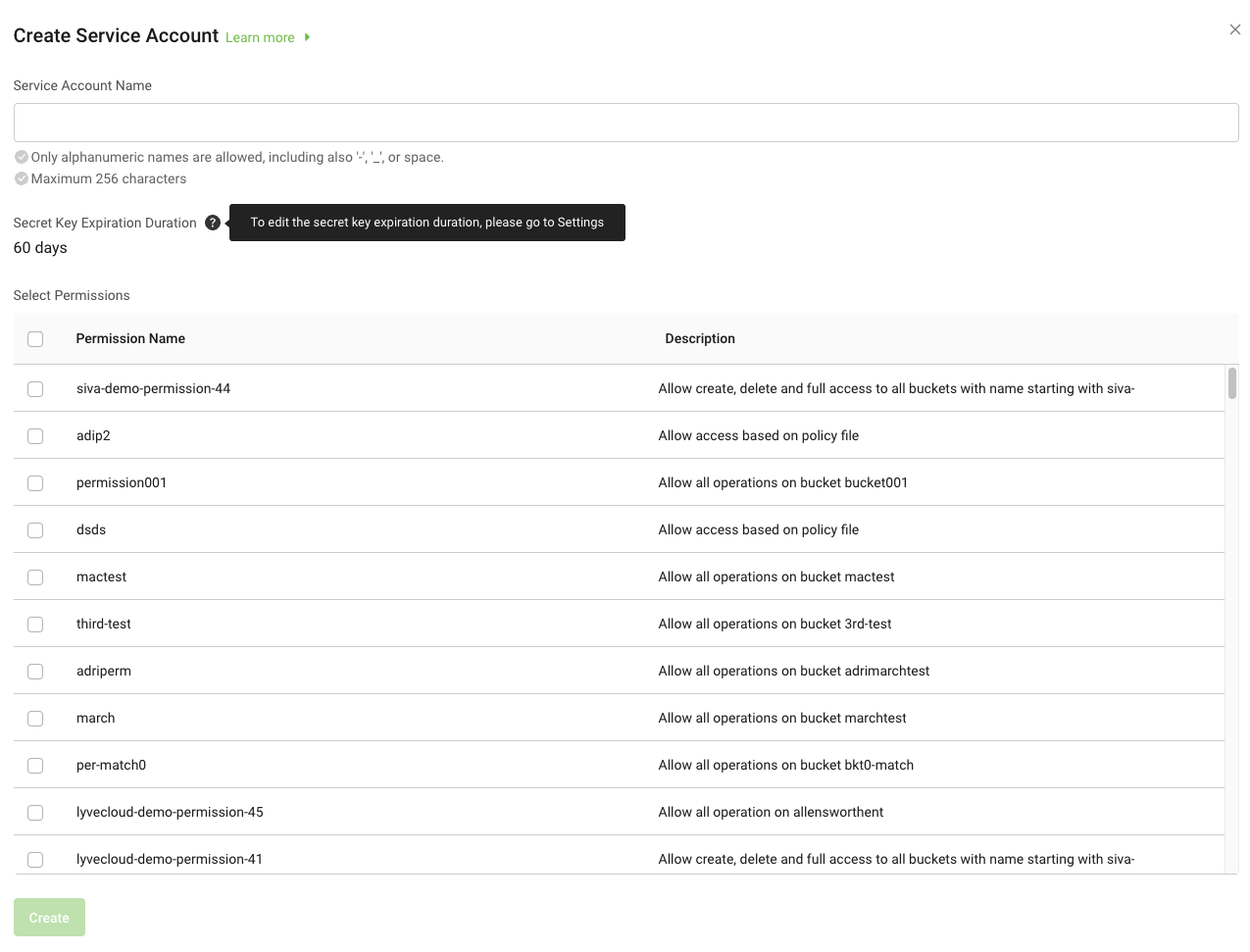
To change the expiration duration, see Setting expiration duration.
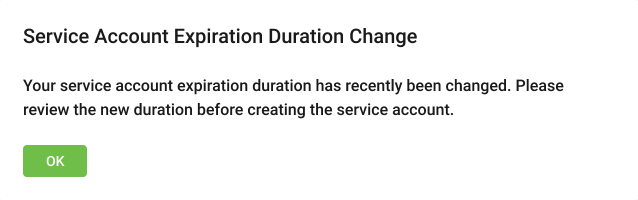
If an administrator configures a new expiration duration during the same time frame as the storage administrator creates a service account, the storage administrator receives an information message about the new expiration duration.
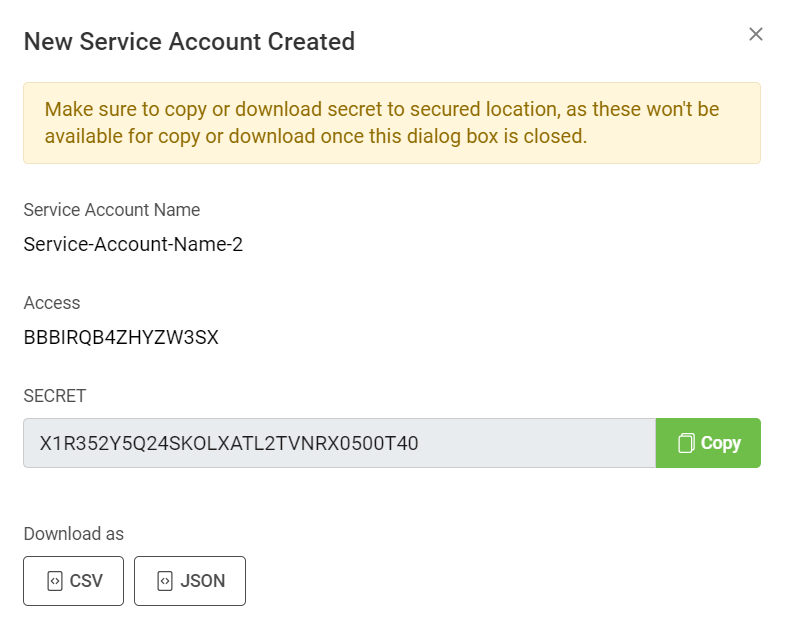
- A confirmation displays the access key and secret keys required to access the bucket.
The following image displays a generated access key and secret key.
Viewing service accounts
The service account list displays the Access Key, expiration period, and the status of the service account.
The 'Expires in' column displays any of the following:
- Expired: If the service account is already expired.
- Never Expires: The expiration period for the service account is not configured.
- Value: Displays the remaining days for the service account to expire.
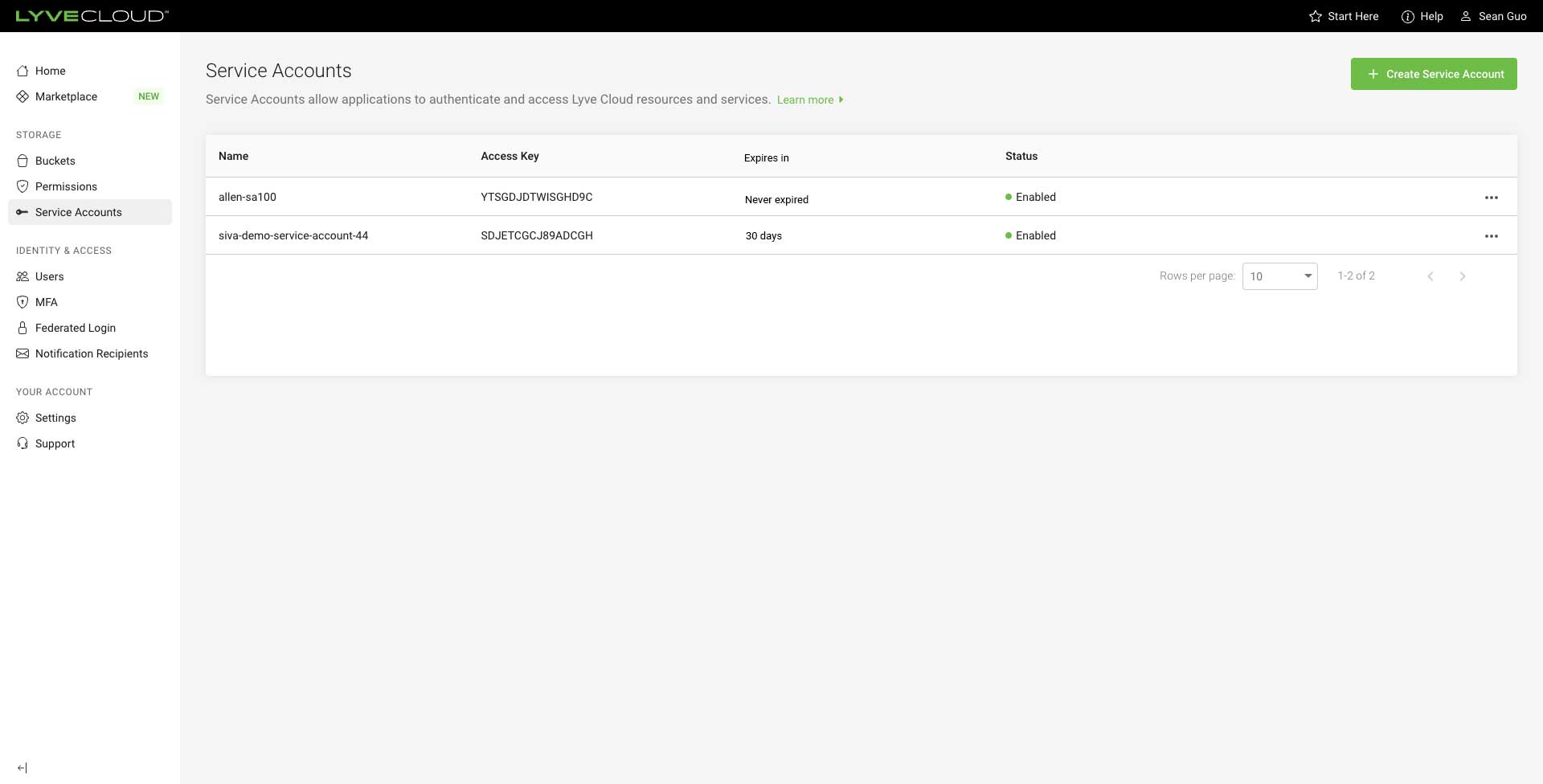
To view the service account list, select Service Accounts on the left-hand menu.
- You can view the list of service accounts.
- You can increase the number of service accounts per page.
- You can change the name from Service_Account_1 to Service_Account_01.
- You can add permission3 (new permission) to permission0, permission1 and permission2 (existing). Or you can remove permission0 (existing) from the available list.
You can perform the following operations by selecting the ellipses for each service account:
Editing service accounts
Editing allows you to edit the service account name and permissions. Editing does not generate a new secret key (credentials) for a service account. To generate new credentials, you must create a new or clone an existing service account. While editing the service account, the access key and expiration period for the service account is displayed. However, you cannot edit them. The expiration period is set when you create a service account. For more information on the expiration period, see Configuring expiration period.
If you edit Service_Account_1: When you save this service account, the name and permission of the service account are changed. However, the secret credentials and expiration period remain the same as the original.
To edit a service account:
- On the left menu, select Service Accounts.
- On the Service Accounts page, select the service account to modify and then select Edit.
- In the Edit Service Account dialog, you can edit the service account name and modify permissions.
- Select or deselect the permissions to associate with the service account, and scroll to view all available permissions for the account.
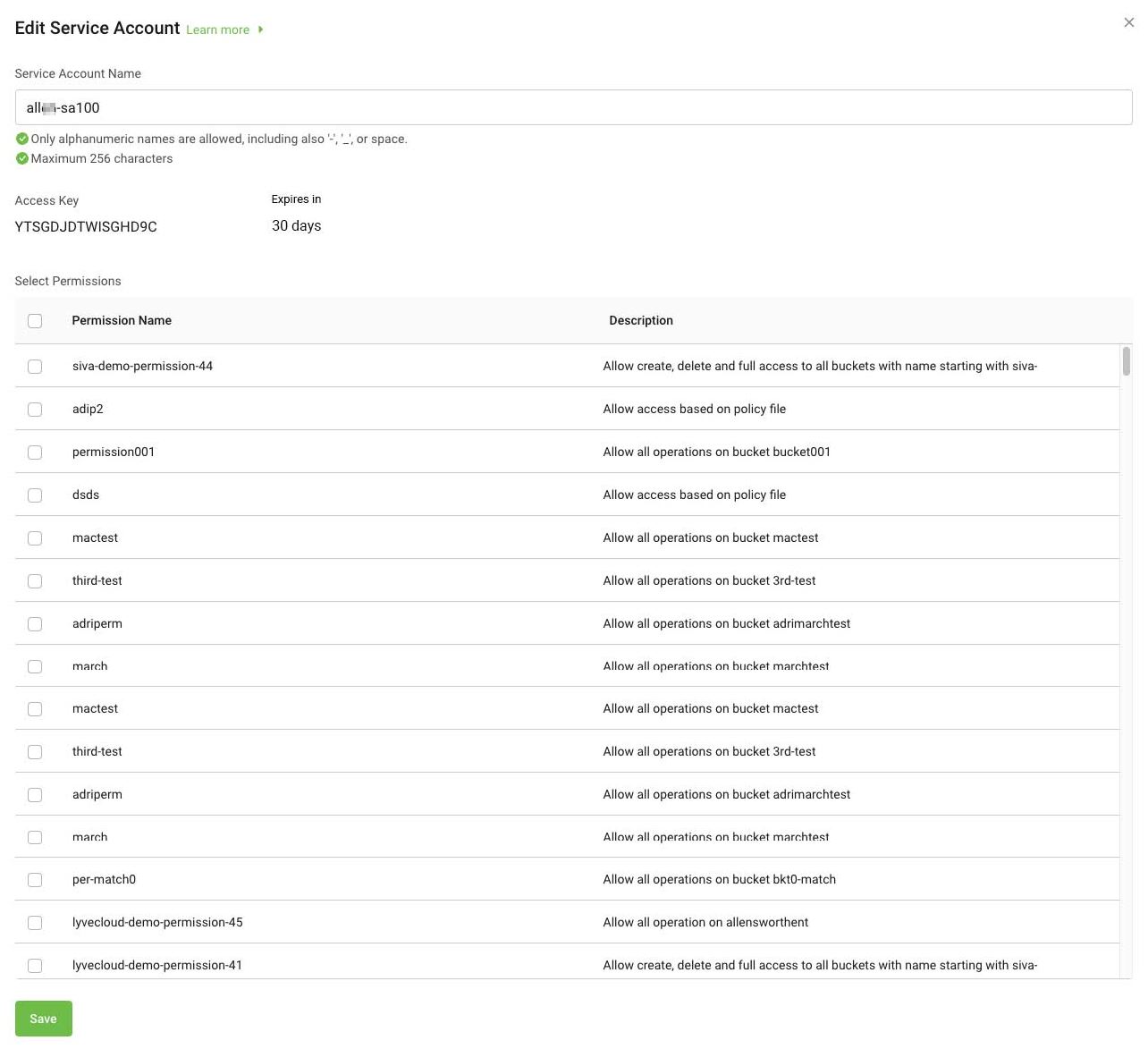
Select Save to save changes for the service account.
Changing the status of a service account
The service account is enabled by default. You can disable the service account anytime. Disabling a service account prevents you from using the secret key to authenticate.
To change the status of a service account:
- On the left-hand menu, select Service Accounts to view the list of service accounts.
- Set Status to Enabled or Disabled to change the account status.
Deleting a service account
Before you delete a service account, you can disable the key, and once you are sure that the service account is no longer needed, you can then delete the key. Deleting a service account permanently prevents you from using the secret key to authenticate.
To delete a service account:
- On the left-hand menu, select Service Accounts.
- On the Service Accounts page, select Delete.
- Select Yes to delete the service account.
You cannot restore a deleted account. However, you can reuse the service account name to recreate a new service account.
Cloning a service account
Cloning a service account is a quick and easy way to create a duplicate service account. The values of the service account, like the service account name, associated permissions, etc., are the same as the original service account. However, it generates new access and secret keys. The name of the service account appears as a Copy of <service account name>, and you can change the name and associate different or same permission to this service account.
To clone a service account:
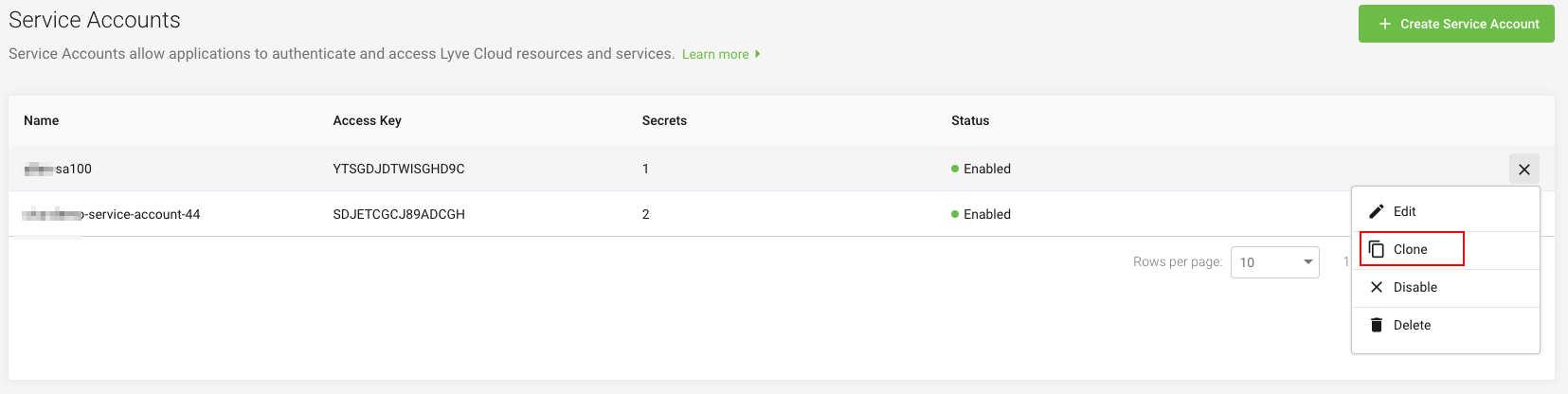
- On the left-hand menu, select Service Accounts to view the list of service accounts.
- Select the ellipses to clone the service account.
- Select Clone, and edit the required fields of the service account.
New secret credentials are generated once you create a service account. For more information, see Creating service accounts.
Service account settings
Adding the expiration duration to the service account enhances the security level of the service account. The existing Service Accounts are set as Never Expires. By default, the key never expires when creating a service account unless you configure an expiration duration. You can change the default setting by setting an expiry duration for all newly created service accounts; see Setting expiration duration. This limits the validity of the service account, which needs to be changed again after the expiration duration. After the expiration date, the secret key cannot be used for authentication but will stay associated with the service account until you delete it. If you disable or delete a service account, any workload that uses the service account will immediately lose access to the resources.
As a best practice, change your secret keys regularly. You can create a new secret key by doing the following:
- Create a new service account or Clone the service account.
- Disable the old service account.
- Confirm that the old key is no longer in use.
- Delete the old service account.
Setting expiration duration
Setting an expiration duration enables you to enforce additional security. The more often you change the service account keys, the less likely it is to be leaked. Hence, periodically invalidating your service account keys and creating new keys adds to security.
The Service Account Expiration defaults to Off (disabled). The service account key never expires when creating a service account without setting an expiration period. You can turn On (enable) the expiration and set the duration in days or years. All service accounts created after you turn on have an expiration period. For example, if you set the expiration duration as 365 days, any service account created after setting the duration has an expiration period of 365 days.
Based on the specified days, the service account expires at the end of the expiration date at 23:59:59 PM, regardless of the time the service account is created. For example, Setting the expiration duration to 30 days on the 1st of the month at 10:15:00 AM, the service account expires on day 30 at 23:59:59 PM.
To set expiration duration:
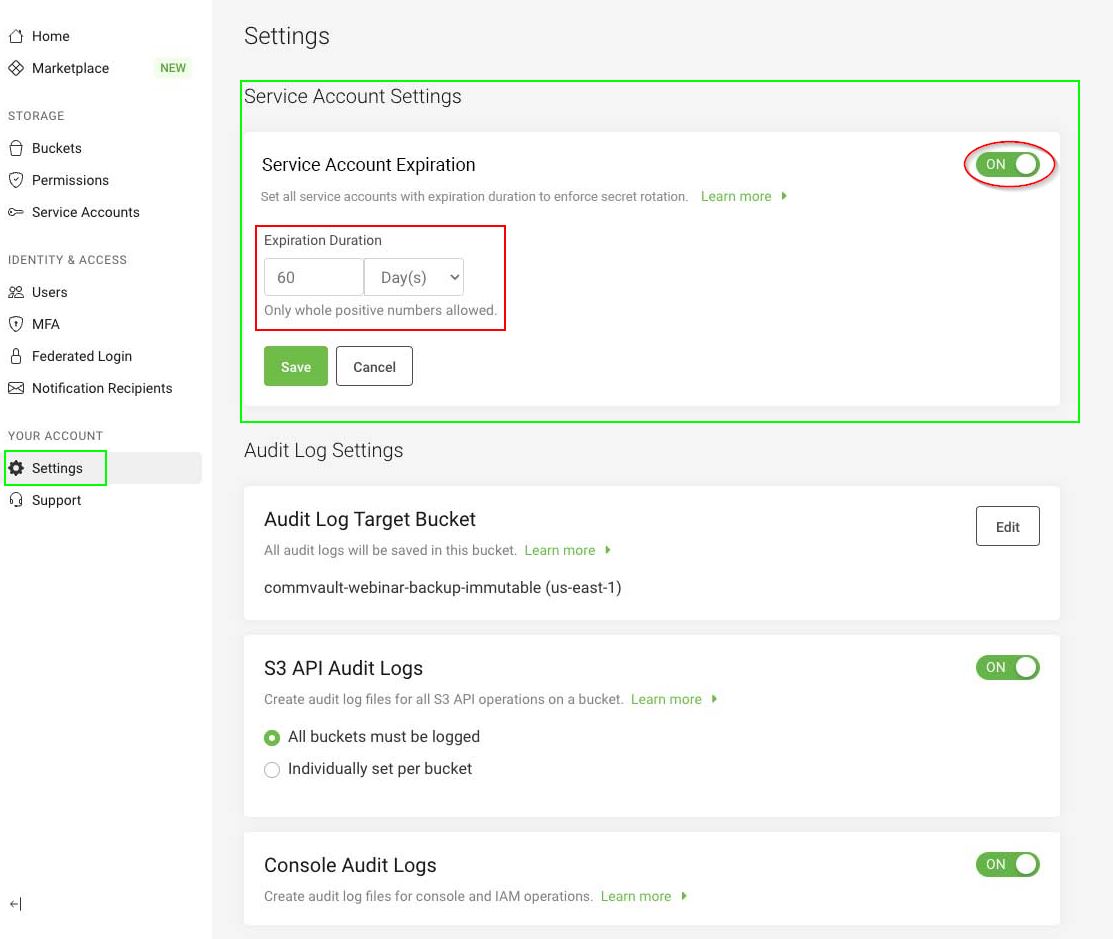
- On the left-hand menu, select Settings.
- Enable the Service Account Expiration toggle.
- Enter the number of Day(s) or Years to set the expiration duration, and select Save.
After the configuration is complete, all new service accounts created will have an expiration duration. Once it expires, you cannot perform any actions; however, you can only delete the service account.
You can configure the expiration duration as 90 days and create a service account. The Secret Key Expiration Duration in the create service account dialogue is set to 90 days. This value is displayed on pages where you create a service account, edit a service account, and list the service account. All service accounts created after configuring expiration duration will be, by default, set to 90 days.
After 90 days, the service account status will appear as Expired.